Password Reset: Volume 3
Oct. 20, 2025
Your Password Is the Key: Protecting Personal Data in the Age of the Dark Web
A few months ago, a mid-sized accounting firm noticed something strange. One of their clients had been locked out of their email. Within hours, fraudulent invoices were sent from their account. The breach didn’t come from malware or a phishing link. It came from a reused password harvested from the dark web.
The attackers paid less than the cost of a cup of coffee for access that could have cost the firm thousands in reputation and revenue. This is the reality of password security today. Understanding how the dark web works and how to protect your data is no longer optional.
“Passwords are still the front door, but we’re finally building smarter locks,” said Rich Miller, founder and CEO of STACK Cybersecurity.
What Is the Dark Web and Why Should You Care?
The dark web is a hidden part of the internet that is not indexed by search engines. It requires special tools like Tor to access and is designed for anonymity. While it can be used for legitimate privacy needs, it is also a haven for hackers who trade in stolen credentials, medical records, and financial data.
Unlike the surface web, where content is regulated and traceable, the dark web is decentralized and unregulated. Once your data appears there, it is nearly impossible to remove. Copies spread quickly across forums and marketplaces, making containment a challenge.
The entire ecosystem is built on anonymity, primarily achieved through networks like Tor and the Invisible Internet Project (I2P). Tor routes user traffic through a series of encrypted relays, effectively masking the user's IP address and location, making it difficult for law enforcement to identify operators on these hidden ".onion" sites.
The Onion’s Many Layers
Websites on the Tor network are called "onion sites" because of Tor's layered encryption system. Like an onion has multiple layers, Tor encrypts data in multiple layers that are peeled away one by one as the data travels through different relay servers.
When you connect to an onion site, your request passes through at least three Tor relays. Each relay only decrypts one layer of encryption, revealing the address of the next relay. No single relay knows both the origin and destination of the data.
Tor relays can be compared to a package being transferred through several intermediaries, with each intermediary only aware of the sender and the next recipient. No single point in the journey knows both who you are and what website you're visiting.
This layered encryption approach provides anonymity for both users and website operators. Onion sites also have special addresses that end with ".onion" instead of traditional domains like ".com" or ".org," making them accessible only through the Tor network.
How Much Is Your Data Worth?
Dark Web Data Pricing reflects market rates for stolen digital information on illicit marketplaces. These platforms, accessible through anonymizing networks like Tor, operate as a hidden economy where data serves as the primary currency.
This pricing structure functions as a real-time threat index, revealing which data types hackers demand most and which assets face the highest risk for businesses. Stolen data is categorized, priced, and sold based on supply, demand, and quality. This ecosystem creates a predictable, albeit illegal, commercial environment.
Cybercriminals treat stolen data like inventory. According to a Dark Web Price, here’s what your credentials might sell for:
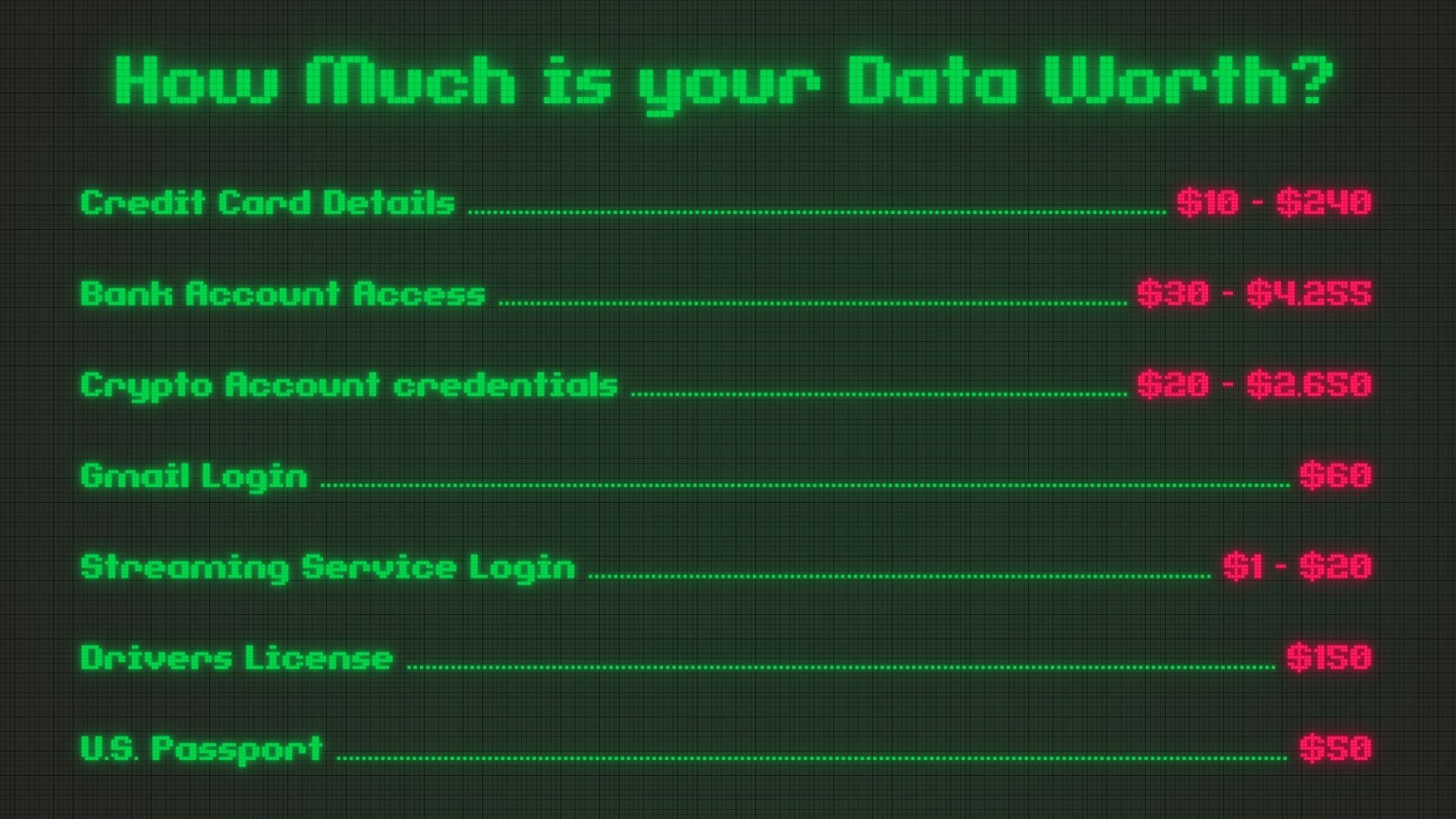
The return on investment is staggering. A hacker can earn thousands from a single data breach, especially when credentials are reused across platforms. One successful phishing campaign can yield hundreds of logins, each with resale value and potential for deeper exploitation.
“You're not just protecting data,” Miller said. “You're protecting actual money and the sacred trust of clients who would absolutely freak out if their financial information ended up on the dark web.”
Can You Remove Data from the Dark Web?
Short answer: not really.
Once personal information is leaked, it is often replicated across multiple platforms. Dark web sites rarely respond to takedown requests, and many operate outside legal jurisdictions. Even if one copy is removed, others persist.
That is why prevention and early detection are critical for identity protection.
Passwords: The First Line of Defense
Passwords are the gateway to your digital identity. Weak or reused passwords are a leading cause of credential theft and data breaches. But here is the twist. Recent guidance from NIST says you no longer need to change them every 90 days.
Updated Guidance from NIST
NIST recommends:
- Do not require periodic password changes unless there is evidence of compromise
- Encourage longer passwords or passphrases instead of complex ones
- Block commonly used or breached passwords
- Avoid password hints and security questions
- Store passwords securely using salted hashing
This shift reflects a move toward usability and security. Frequent resets often lead to weaker passwords. Instead, focus on creating strong, memorable passphrases.
Example: Coveted3-P0lka-B@bbling-Dodge-Golden
Proactive Protection Strategies
Even if your data ends up on the dark web, you can still take action.
Use a Password Manager
Tools like Keeper securely store and generate complex passwords. They also support compliance with frameworks like NIST 800-171 and CMMC.
Enable Multi-Factor Authentication (MFA)
MFA adds a second layer of security, making it harder for attackers to access your accounts even if they have your password.
Monitor the Dark Web
Services that scan the dark web can alert you if your credentials appear. Early detection allows for faster response.
Remove Yourself from Data Brokers
Data brokers collect and sell personal info. Use services like Optery or Privacy Bee to opt out and reduce your exposure.
What to Do If You’re Compromised
If your information is found on the dark web:
- Change all passwords immediately
- Enable MFA on every account
- Monitor financial and identity activity
- Use breach monitoring tools
- Contact your IT or security team for support
What’s Next for Passwords?
The password as we know it is evolving. While strong passphrases and multi-factor authentication remain essential, the future is moving toward passwordless authentication and behavioral biometrics.
Passwordless Authentication and SSO
Technologies like Windows Hello, FIDO2, and passkeys are gaining traction. These systems use device-based credentials, biometrics, or cryptographic keys to authenticate users without requiring a traditional password. This reduces phishing risk and improves user experience.
At STACK Cybersecurity, we use Single Sign-On (SSO) for nearly everything. This means our team logs in once and gains secure access to multiple platforms without juggling dozens of passwords. SSO is a practical step toward passwordless authentication, reducing friction while improving security.
“SSO isn’t just convenient,” said Tracey Birkenhauer, Vice President of STACK Cybersecurity. “It’s strategic. It lets us enforce strong authentication without relying on users to remember complex passwords for every tool they use.”
Behavioral Biometrics
Instead of relying solely on what you know, behavioral biometrics analyze how you type, swipe, or move your mouse. These patterns are unique and difficult to replicate, making them a powerful layer of identity verification.
AI-Powered Threat Detection
Artificial intelligence is being used to detect compromised credentials in real time. By analyzing login patterns and anomalies, AI can flag suspicious activity before damage is done.
Dark Web Monitoring as a Standard
Dark web scans are becoming a routine part of cybersecurity best practices. Organizations are increasingly integrating breach detection tools into their security stacks to catch exposed credentials early.
“We’re past the point of hoping passwords don’t leak,” Miller said. “The question now is how fast you can respond when they do.”
Beyond Passwords: What Comes Next
As organizations move toward passwordless authentication, the conversation is expanding to include verifiable digital credentials—secure, portable identity tokens that go beyond usernames and passwords. These credentials can be used to prove employment, certifications, or access rights without exposing sensitive data.
If you're curious about how digital credentials are shaping the future of identity management, check out our post about digital credential essentials.
It explores how decentralized identity systems are changing the way we verify who we are online, and why this matters for cybersecurity, compliance, and user experience.
Final Thoughts: Prevention Is Power
The dark web is not going away. But your data does not have to end up there. By strengthening your password hygiene, using privacy tools, and staying informed, you can protect your identity and your peace of mind.
“Cybersecurity is like dental hygiene,” Miller likes to say. “It’s not particularly exciting, but ignore it and things get really unpleasant really fast.”
If you are unsure where to start, STACK Cybersecurity offers personalized guidance and tools to help you secure your digital footprint.
Related Resources
- Password Reset: Volume 1
- Password Reset: Volume 2
- Password Reset: Volume 4
- Onboard and Optimize Your Password Manager
- New Password Guidance Shifts Toward Simplicity, Security
- How to Remove Browser Passwords for Heightened Security
Need help optimizing your passwords?
Call (734) 744-5300 or Contact Us to schedule a consultation with our team of professionals.
