New Password Guidance: A Shift Toward Simplicity and Security
Oct 11, 2024
Passwords remain a common method of authentication, despite usability and security concerns. People often struggle to remember complex, arbitrary passwords, leading them to choose easily guessable ones. This also leads to password repetition across multiple accounts.
Research shows users respond in predictable ways to password requirements. For example, a user who logs in with “password” as their password would be likely to use “Password1” if required to include an uppercase letter and number.
To mitigate security risks, online services have implemented complexity rules, such as requiring a mix of character types such as digits, uppercase letters, and symbols. However, studies of breached password databases confirm these rules offer limited security and decrease memorability.
The National Institute of Standards and Technology (NIST) has recently updated its password security guidelines, marking a significant departure from traditional practices. These changes, outlined in NIST Special Publication 800-63B, aim to enhance cybersecurity while improving user experience.
Key Password Guideline Changes
- Emphasis on Password Length Over Complexity: NIST now recommends focusing on password length rather than complexity. The new guidelines suggest a minimum password length of 8 characters, with a strong preference for even longer passwords, up to 64 characters. This shift is based on the understanding that longer passwords are generally more secure and easier to remember.
- Elimination of Mandatory Periodic Password Changes: One of the most notable changes is the removal of mandatory periodic password changes. NIST argues frequent password resets often lead to weaker passwords and encourage users to make minor, predictable changes. Instead, passwords should only be changed when there is evidence of compromise.
- Blocking Commonly Used or Compromised Passwords: NIST emphasizes the importance of checking passwords against lists of commonly used or compromised passwords. Organizations are advised to maintain an updated blocklist of weak passwords and prevent users from selecting any password on this list.
- Discouraging Password Hints and Knowledge-Based Authentication: The new guidelines advise against using password hints or knowledge-based authentication questions, as these can often be easily guessed or discovered through social engineering.
- Enhanced Password Storage Practices: For storing passwords, NIST recommends using salted hashing with a work factor that makes offline attacks computationally expensive. This approach helps protect stored passwords even if a database is compromised.
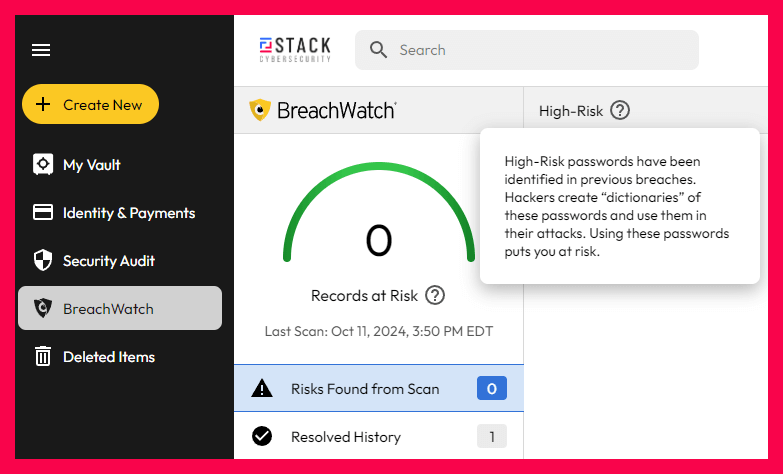
Password managers such as Keeper Security allow users to create and store passwords. More importantly, Keeper provides lists of reused, breached, and weak passwords. Users are alerted to these issues as are Keeper administrators. For organizations that outsource their cybersecurity, their managed security service provider (MSSP), such as STACK Cybersecurity, also receives these notices and encourages their clients to follow best practices.
See the BreachWatch dashboard below.
These NIST password updates are designed to reflect a more user-friendly approach to cybersecurity. By prioritizing password length and eliminating unnecessary complexity, NIST aims to reduce the burden on users while enhancing overall security. The focus on blocking weak passwords and improving storage practices further strengthens these guidelines.
Many password-related attacks, such as keylogging, phishing, and social engineering, are just as effective against long and complex passwords as they are against simple ones. These types of attacks bypass the benefits of password complexity and length, highlighting the need for additional security measures.

“Keeper password manager is like having a personal security guard for your organization's most sensitive information," said Peter Lekas, Inside Sales Executive at Keeper Security. "It not only simplifies employee password management but also enhances security by promoting strong, unique passwords for every account — protecting your data from breaches and ensuring peace of mind in an increasingly dangerous digital world.”
Password Policy
Implementing a NIST password policy can actually ease the burden on organizations. Unlike many security measures, it enhances user experience by removing complex password rules and reducing the need for frequent password changes. This approach also cuts administrative costs by decreasing the number of password reset calls and enabling automated remediation. Moreover, it boosts security by adhering to modern industry standards for password management.
With the multitude of accounts users must balance, and the varying requirements across accounts, a password manager remains the simplest and more secure approach to password generation, storage, and filling. A password manager generates strong and unique passwords and passphrases for every account, secures them with end-to-end encryption, and automatically fills them to protect against attacks such as keylogging. Furthermore, a password manager can generate and automatically fill strong forms of multi-factor authentication, providing a critical additional layer of defense.
In summary, NIST’s new password guidelines represent a significant step forward in balancing security and usability. However, a password manager can further reduce the burden on individuals and organizations alike, promoting adherence to best practices and increasing user adoption. It takes a holistic approach for organizations to protect their systems and data while providing a seamless user experience.
