
Incident Response Best Practices: How STACK Cybersecurity Protects Your Business
Dec 18, 2024
Cyberattacks are growing more sophisticated, and the speed at which they occur demands immediate action. Responding to cybersecurity incidents in-house can be overwhelming for small and medium-sized businesses, especially without a dedicated team or the right tools.
That’s where STACK Cybersecurity steps in.
With a Managed Security Service Provider (MSSP) like us, you don’t have to navigate incident response alone. Our team monitors, detects, and responds to threats in real-time, minimizing risks to your operations and reputation. In this post, we’ll break down the critical components of incident response, the six phases of managing an incident, and best practices to protect your business.
What is Incident Response?
Incident response is the process of identifying, managing, and mitigating cybersecurity threats such as ransomware, phishing, or data breaches. The goal is to minimize damage, restore operations, and reduce the likelihood of future incidents.
Why Businesses Need an Incident Response Plan
Cybersecurity incidents can have severe consequences, including financial losses, operational downtime, and reputational harm. A strong incident response plan (IRP) helps:
Protect Sensitive Data: client and business information during an attack.
Preserve Business Continuity: Minimizing downtime and disruptions
Meet Compliance Requirements: Addressing standards like CMMC, SOC 2, and NIST.
Mitigate Financial Impact: Reducing costs associated with breaches, including potential fines.
Build Trust: Demonstrating a proactive approach to cybersecurity for clients and stakeholders.
Components of an Incident Response Plan
Here are the critical components of an incident response plan (IRP) that helps organizations respond more effectively to a breach:
- Incident Response Team: A cross-functional team responsible for executing the incident response plan, including IT, legal advisers, communications professionals, and leadership.
- Incident Classification and Escalation: A defined criteria for categorizing incidents based on severity and impact, ensuring an appropriate response level.
- Response Procedures: Instructions for handling incidents, from initial detection to restoration of business operations.
- Communication Protocols: Clear guidelines for internal and external communication, including notifying stakeholders, regulators, or customers.
- Post-Incident Review: A process to analyze what happened, evaluate the response, and identify areas for improvement.
Why is Incident Response Important?
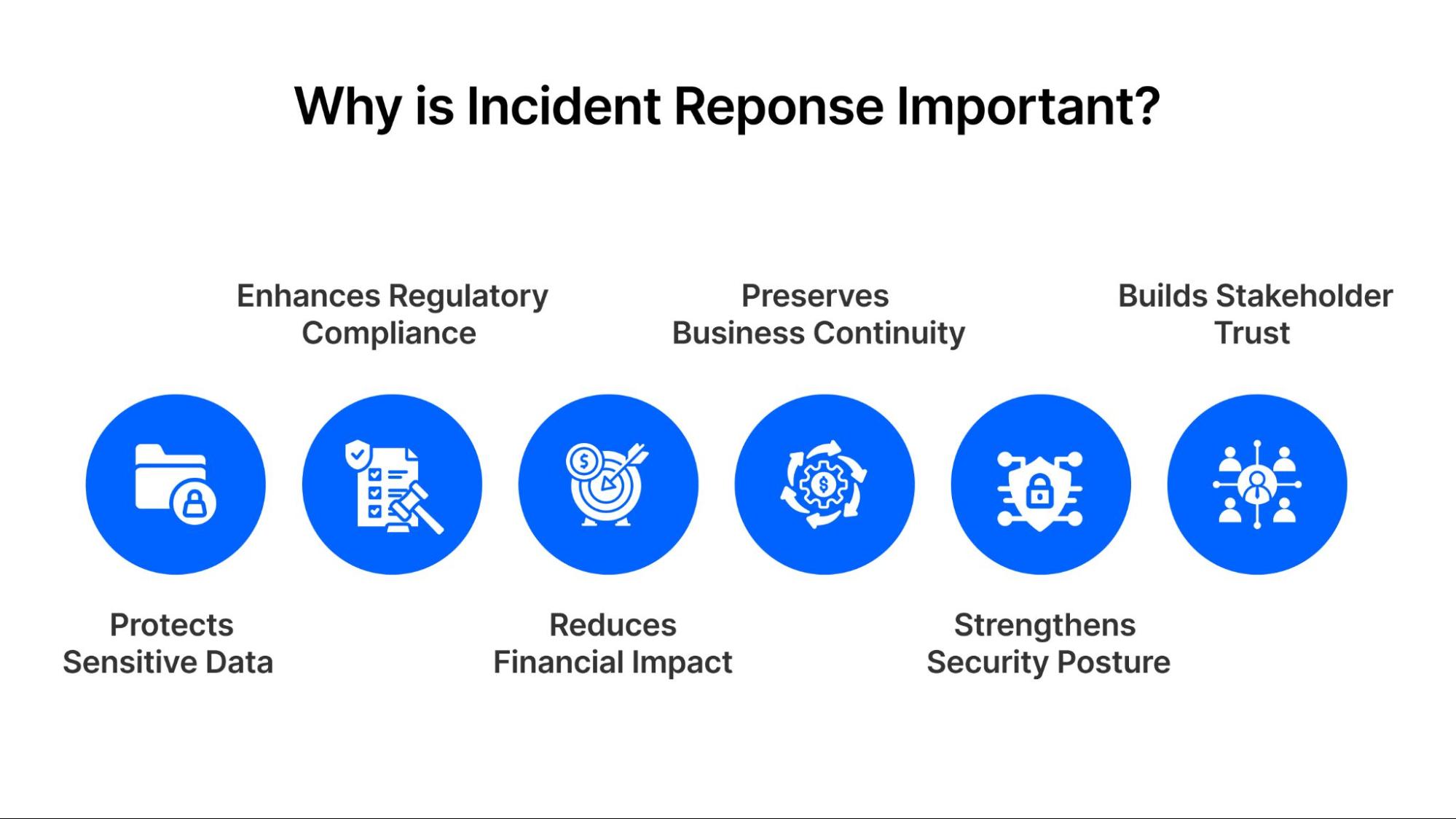
Incident response helps to safeguard an organization’s operations, data, and reputation. Here’s a detailed look at why incident response is vital for businesses:
Protects Sensitive Data
Client information, intellectual property (IP), and employee records, are often the primary target of cyberattacks. An effective response can prevent attackers from accessing or exfiltrating valuable information in a data breach. This minimizes immediate harm and demonstrates to customers and stakeholders your organization takes data protection seriously.
Additionally, preserving sensitive data prevents the financial and operational fallout of recovery efforts, legal battles, and loss of trust. Organizations that invest in incident response safeguard their reputation by showing they can defend against threats.
Enhances Regulatory Compliance
Regulatory compliance is a non-negotiable aspect of business operations with the proliferation of data protection laws such as SOC 2, CMMC, and NIST. Incident response is integral to meeting these compliance requirements, as many regulations mandate prompt reporting and effective handling of data breaches.
Failing to report a data breach within the prescribed timeframe can lead to hefty fines and legal actions. Companies with strong incident response strategies can demonstrate accountability by documenting their efforts to manage incidents effectively, providing the transparency regulators demand.
Reduces Financial Impact
The financial implications of a cybersecurity incident can be damaging, ranging from ransomware payments and legal fees to indirect costs like reputational damage and lost business. Incident response mitigates these losses by enabling swift threat containment and minimizing the duration and extent of the attack. For instance, stopping a ransomware attack early prevents the spread of malware to additional systems, reducing downtime and safeguarding critical operations.
Furthermore, organizations that demonstrate preparedness through incident response are often better positioned to negotiate lower cybersecurity insurance premiums, providing long-term financial benefits.
Preserves Business Continuity
Downtime caused by a cyberattack can have far-reaching effects, such as disrupting supply chains and eroding customer confidence. Incident response ensures organizations recover quickly and continue their operations with minimal interruption. By implementing pre-defined processes and using trained personnel, businesses can restore critical systems and data efficiently, often within hours rather than days or weeks.
This rapid recovery protects revenue streams and reinforces customer loyalty, as stakeholders can see the organization’s resilience and dedication to maintaining service quality. In industries where reliability is essential, such as legal or finance, preserving business continuity can be the difference between retaining and losing customers.
Strengthens Security Posture
Incident response should not be a reactive measure. It’s the foundation of proactive cybersecurity. Each incident provides valuable insights into vulnerabilities, attack methods, and gaps in current defenses. By analyzing these insights, companies can refine their strategies, implement stronger controls, and better prepare for future threats.
Builds Stakeholder Trust
How an organization handles cybersecurity incidents can significantly impact its relationships with customers, partners, and investors. A clear and professional response reassures stakeholders of the organization’s competence and reliability, while a poorly managed incident can damage trust and harm its reputation in the long term.By prioritizing incident response, organizations protect their stakeholders’ interests and establish themselves as leaders who take security and accountability seriously.
The Six Phases of Incident Response
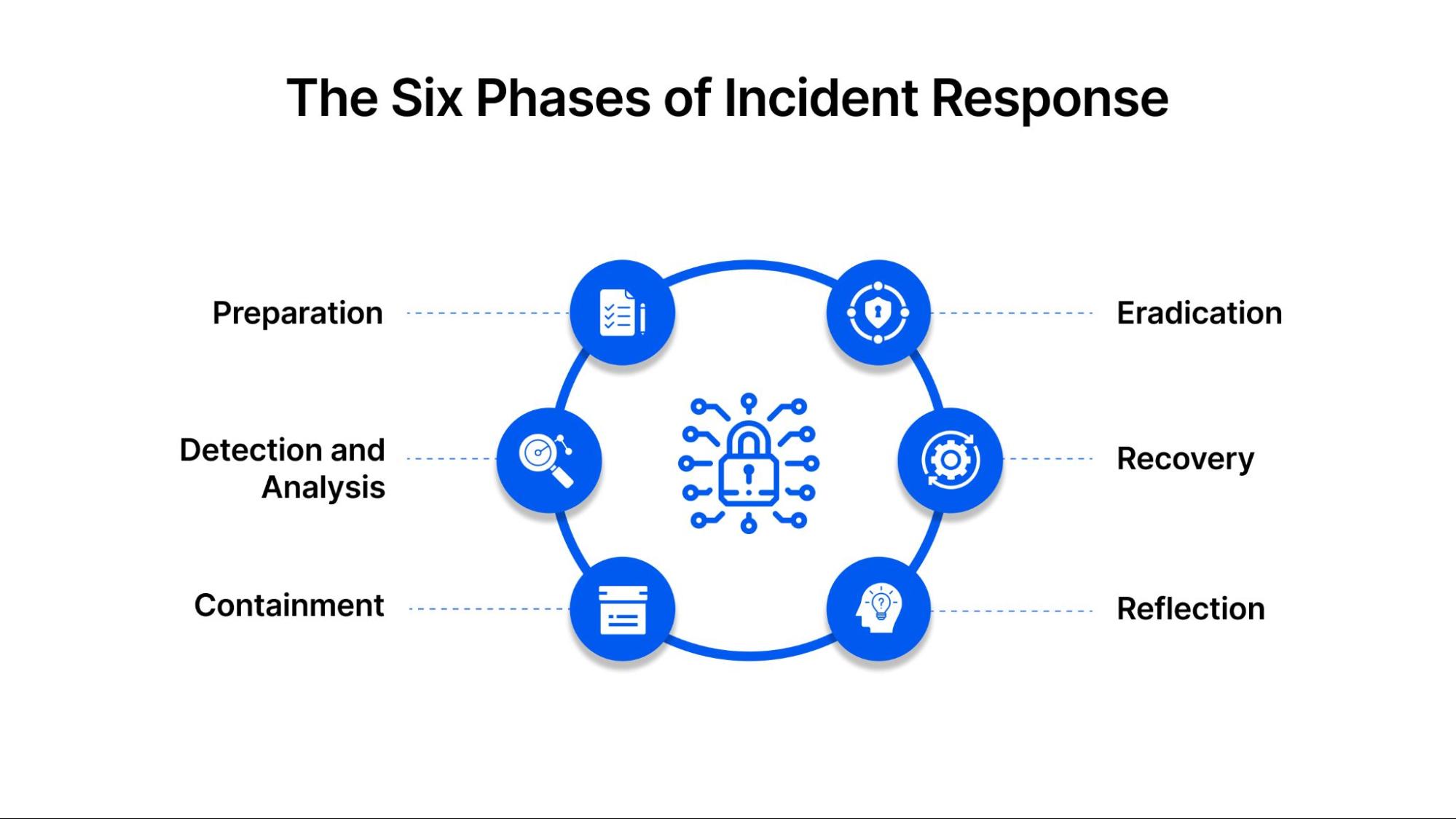
At STACK Cybersecurity, we align our processes with industry standards to deliver a seamless incident response strategy for our cybersecurity clients:
- Preparation: We develop and maintain tailored incident response plans and playbooks, ensuring all roles, responsibilities, and tools are ready to go.
- Detection and Analysis: We use advanced tools like Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) to monitor your systems 24/7 and quickly identify potential threats.
- Containment: When an incident is detected, we act swiftly to isolate affected systems, limiting the attack’s spread.
- Eradication: Our team investigates and eliminates the root cause of the incident, ensuring no residual threats remain.
- Recovery: We restore your systems and operations with minimal downtime, implementing measures to prevent future attacks.
- Post-Incident Review: After every incident, we evaluate our response to strengthen your defenses and refine your security strategy.
Incident Response Best Practices
STACK Cyber implements proven strategies to protect our clients, including:
- Regularly Updating Incident Response Plans: Adapting to emerging threats and lessons learned
- Conducting Real-World Simulations: Testing response protocols through tabletop exercises and mock attacks
- Deploying Cutting-Edge Detection Tools: Leveraging SIEM and EDR solutions for continuous monitoring.
- Establishing Clear Communication Protocols: Ensuring seamless communication during and after an incident.
- Documenting Every Step: Creating a detailed record of actions taken for compliance and analysis.
- Promoting a Security-First Culture: Empowering employees to identify and report threats effectively via cybersecurity awareness training and updates regarding the latest threats.
Mitigate Cybersecurity Incidents with STACK Cybersecurity

STACK Cybersecurity with clients to provide comprehensive protection against cyber threats.
What We Offer
- Managed Incident Response: Our Managed eXtended Detection and Response (MXDR) allows us to remove the burden from our clients’ teams, responding to incidents swiftly and effectively. Advanced Monitoring and Detection: Our tools, such as Security Information and Event Management (SIEM), help us identify, prevent, and remediate threats.
- Compliance Support: We help your business meet industry regulations like CMMC and SOC 2 Type 2.
- Proactive Defense Strategies: From vulnerability assessments to real-time threat detection, we ensure your business is secure.
Improve Your Cybersecurity
Cybersecurity is a shared responsibility—but with STACK Cybersecurity, the heavy lifting is on us. Let us help you safeguard your data, reputation, and operations.
Act fast and stay secure.
Schedule a Consultation
