
Conducting a Cybersecurity Audit: Steps and Considerations
Dec 19, 2024
Is your business prepared to tackle the growing risks of cyber threats? You might think so, but here’s a surprising fact: only 70% of large companies include cyber risks in their internal audits. For smaller companies, that number drops to just 40%. This means many businesses are exposed to vulnerabilities that could result in data breaches, financial losses, or reputational damage.
Despite growing awareness and the implementation of advanced technological and procedural defenses, cybercrime continues to rise. The research paper Effectiveness of cybersecurity audit shows chief audit executives identify cybersecurity as one of the top five business risks.
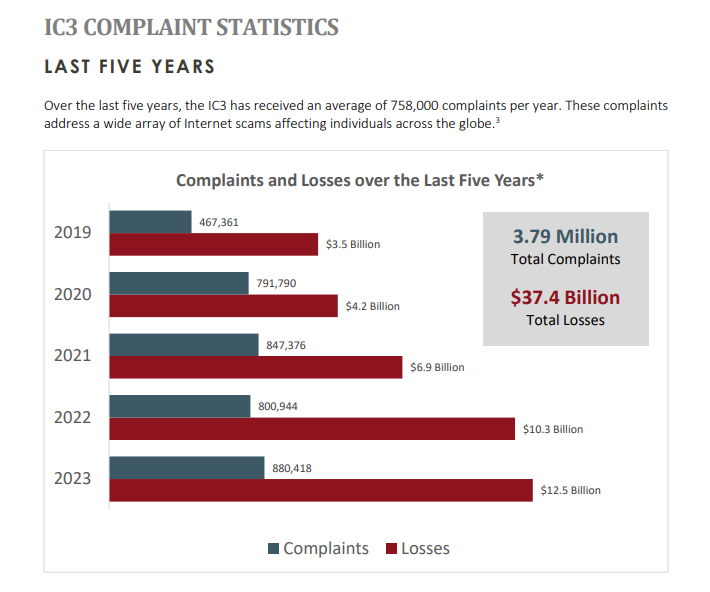
In 2023, the FBI’s Internet Crime Complaint Center (IC3) received a record 880,418 complaints, marking a nearly 10% increase from 2022. The reported losses exceeded $12.5 billion, a 22% increase compared to the previous year. Additionally, the number of hacking intrusion attempts in 2023 reached 7.6 trillion, a 20% increase from 2022. These statistics highlight the growing threat and need for auditable cybersecurity measures. Review the Internet Crime Report 2023.
Cybersecurity audits (CSAs) are more than just a formality—they’re essential for identifying weaknesses, ensuring regulatory compliance, and strengthening defenses against potential attacks. Without them, companies risk overlooking blind spots that attackers are too eager to exploit.
This blog will explain cybersecurity audits, their essentials, and how often they should be conducted.
What is a Cybersecurity Audit?
Think of a cybersecurity audit as your business’s digital health checkup. It systematically evaluates your IT infrastructure, policies, and practices to ensure they align with industry standards and safeguard sensitive data.
A cybersecurity audit goes beyond identifying weaknesses. It provides a clear snapshot of your security posture, highlights vulnerabilities, and offers actionable insights to strengthen defenses. Whether checking for outdated software, reviewing user access controls, or analyzing network configurations, every aspect of your cybersecurity landscape is scrutinized.
The role of the internal cybersecurity audit is to ensure those primarily responsible for cybersecurity risk management have used their resources to the fullest extent possible. Traditionally, internal audit teams have focused only on financial and operational risks. Adding cybersecurity to these responsibilities presents significant challenges.
Many audit teams find it difficult to define the scope of cybersecurity audits (CSA), partly because the information security function also handles assurance and partly because boards of directors often struggle to set clear expectations for mitigating cyber risks. There is also concern that internal auditors lack the necessary skills, knowledge, and resources to effectively review the emerging cybersecurity risk management area.
This is particularly challenging for small and mid-sized companies that typically don’t have dedicated IT auditors. That’s why these businesses typically outsource the IT audit function to Managed Security Service Providers (MSSPs) like STACK Cybersecurity.
Why Do You Need a Cybersecurity Audit?
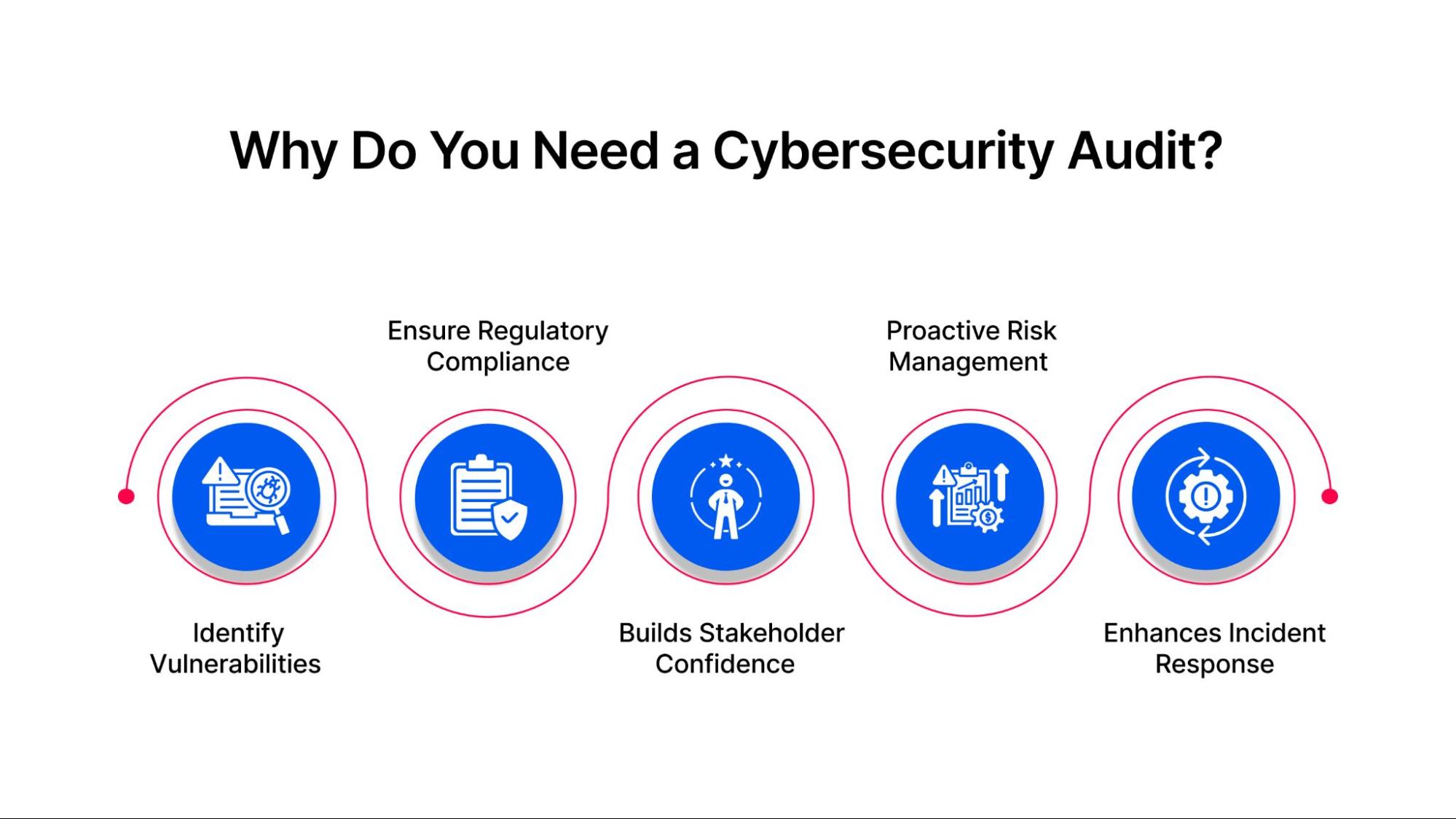
A cybersecurity audit is like taking stock of your digital defenses—it’s a way to examine your systems are safe, functional, and prepared for anything. For many businesses, an audit isn’t just helpful; it’s a practical step toward preventing costly mistakes and bolstering long-term stability. Here’s why it matters:
Identify Vulnerabilities
A cybersecurity audit is like a detective’s magnifying glass, meticulously examining aspects of your IT environment to reveal potential weaknesses. These vulnerabilities might include something as simple as employees using weak passwords or as complex as misconfigured firewalls and outdated software.
Consider a growing business with stretched IT resources. It’s easy for such a company to miss critical software updates or leave old, unused accounts with administrator access. A cybersecurity audit identifies these gaps and provides actionable steps to address them, helping to prevent incidents like data breaches or ransomware attacks before they happen.
Ensure Regulatory Compliance
You likely have regulations to follow if your business handles sensitive information—customer payment details, patient records, or internal financial data. From SOC 2 Type 2 to CMMC, industry standards exist to protect data. Non-compliance isn’t just risky; it can result in fines, lawsuits, and a tarnished reputation. These regulations mandate regular cybersecurity assessments to ensure sensitive information is handled securely.
Beyond compliance, audits help organizations navigate regulation complexities. For example, health care providers must ensure all patient records are securely stored and encrypted. An audit helps confirm these processes are in place and provides the necessary documentation if regulators come calling. It’s a way to avoid unpleasant surprises while showing your customers and stakeholders you take their trust seriously.
Builds Stakeholder Confidence
Customers, partners, and investors need assurance their data is secure with you. A cybersecurity audit demonstrates you’ve taken the necessary steps to protect sensitive information, proving your commitment to data security goes beyond mere promises.
Building trust through audits is essential for businesses looking to grow or expand. It shows you're prepared to face cybersecurity challenges head-on and strengthens your standing in an increasingly competitive market.
Proactive Risk Management
Cyber threats are always evolving. In fact, 62% of leaders anticipate employees will fall victim to AI-driven attacks. Hackers are developing more sophisticated ways to bypass standard security measures, and what worked last year might not protect your organization today. A cybersecurity audit helps you stay ahead by identifying potential risks before they become serious issues.
For example, if you recently transitioned to a cloud-based system, there could be new vulnerabilities to address, like insecure access points or misconfigurations. An audit helps identify and resolve these issues so you’re not caught by surprise in the future.
Enhances Incident Response
Even with strong defenses, security incidents can happen. What’s critical is how well your business responds to these breaches. A cybersecurity audit evaluates your incident response plan, identifying gaps and recommending improvements.
For instance, an audit might reveal that your agency lacks a clear protocol for reporting breaches, leading to delays in mitigation. It might also uncover that your backup systems aren’t configured correctly, leaving your company vulnerable to data loss during a ransomware attack. With this insight, you can refine your processes, ensuring a swift and efficient response. Fixing these gaps after an audit makes your response smoother, minimizing damage if something goes wrong.
Cybersecurity audits aren’t about scaring you into action—they’re about giving you a clear picture of your systems and the confidence to make improvements where needed. In short, they’re a practical investment in your organization’s safety and success.
How Often Should You Consider a Cybersecurity Audit?
There’s no one-size-fits-all answer here—it depends on your industry, size, and risk exposure. However, a few general guidelines can help
Annually as a Baseline
Conducting a cybersecurity audit at least once a year is a practical starting point for most businesses. This annual checkup allows you to evaluate your systems, policies, and processes against the latest security standards and threats.It helps identify outdated practices, like using unsupported software or failing to rotate passwords, that could become weak points over time. For organizations with moderate risk exposure, this strikes a good balance between maintaining security and managing resources efficiently.
However, businesses operating in high-risk environments, such as financial institutions or e-commerce platforms, might require audits more frequently. Cyber threats targeting these industries are often more sophisticated, and annual reviews may not be enough to keep pace.
After Significant Changes
It’s critical to reassess your security posture whenever your company makes significant changes. Changes like implementing new software, integrating third-party services, migrating to the cloud, or expanding your physical office network can introduce vulnerabilities.
Skipping an audit after significant changes can expose your business to threats you didn’t anticipate. It’s always better to catch vulnerabilities early rather than deal with the fallout of a breach later
When Compliance Requires It
Specific industries are governed by strict regulatory requirements that dictate how often cybersecurity audits should occur. For example, healthcare providers handling sensitive patient data under HIPAA must conduct regular assessments to meet privacy and security standards. Similarly, organizations processing credit card payments must adhere to PCI DSS guidelines, which include periodic reviews.
These audits aren’t just about avoiding penalties—they’re also an opportunity to ensure your systems meet the latest industry standards. Falling behind on compliance can lead to legal complications, fines, and damage to your reputation. Proactively scheduling audits to align with regulatory timelines helps you stay on top of these obligations without scrambling to meet deadlines.
Following a Security Incident
A cybersecurity breach signals that something in your defenses needs attention. Whether it’s a ransomware attack, phishing incident, or data breach, conducting a post-incident audit is essential to understanding what went wrong and how to prevent it from happening again.
A thorough audit after an incident does more than assess the damage. It helps trace the root cause of the attack, whether that’s a misconfigured firewall, an unpatched vulnerability, or human error. The findings from this audit should guide immediate improvements, such as tightening access controls, updating software, or enhancing employee training on cybersecurity best practices.The sooner you perform an audit after an incident, the better. Quick action can help rebuild trust with stakeholders and minimize long-term damage to your organization.
Creating a Culture of Regular Audits
Cybersecurity is not a one-and-done task—it requires ongoing attention. Incorporating audits into your organization’s routine operations helps create a culture of vigilance and accountability. Rather than treating audits as a reactive measure, they become a proactive way to stay ahead of threats.
For some organizations, this might mean quarterly or biannual audits, especially if they face high levels of risk or handle sensitive data. Others might schedule smaller, focused assessments throughout the year alongside a more comprehensive annual review. Ultimately, the goal is to include cybersecurity audits in your operational calendar regularly.
A cybersecurity audit isn’t just a test of your defenses; it’s an opportunity to gain expert insights and improve your organization’s security. By preparing thoroughly, you make the process smoother, demonstrate your commitment to security, and ensure that the audit delivers maximum value.
Transform Your Security Posture with STACK Cybersecurity.

A cybersecurity audit is the first step to identifying vulnerabilities and building a stronger defense. STACK Cybersecurity is your dedicated partner for navigating these cybersecurity challenges. With 20+ years of expertise in cybersecurity, we address today’s most pressing cybersecurity needs, helping businesses like yours protect what matters most—your data.
For a cybersecurity audit (CSA) to be effective, the skills and knowledge of the auditors are crucial. While the importance of the internal auditors' competence is well-documented, there's a concern that if they follow practices just to meet standards, they might only achieve "good enough" results rather than truly effective ones. In cybersecurity, auditors need to go beyond just ticking boxes.
A recent study, Key drivers of cybersecurity audit effectiveness: A neo-institutional perspective, examined three sources of internal auditors' professional knowledge: academic background, cybersecurity certifications, and training. It found the internal auditors' certifications, along with a board of director's expertise in cybersecurity, play a decisive role in CSA effectiveness.
The analysis showed the board's competence is closely linked to its support for the audit team, whether it be an existing internal team or an outsourced MSSP. This support includes dedicating time to CSA in meetings, providing clear requirements, ensuring adequate resources, and allowing sufficient time for the audit team to conduct CSAs
Moreover, partnering with a Managed Security Service Provider (MSSP) can further enhance the effectiveness of a cybersecurity audit. MSSPs bring specialized expertise and resources that many internal teams lack. They stay up-to-date with the latest threats and technologies, ensuring your cybersecurity measures are current and robust.
MSSPs can provide a more comprehensive and objective assessment, leveraging their experience across various industries to identify and mitigate risks more effectively. This partnership allows your internal team to focus on core business functions while ensuring a strong cybersecurity posture.
Our services go beyond IT support; we bring a powerful stack of industry-leading tools and expertise. From ?Managed eXtended Detection and Response (MXDR) to Security Information and Event Management (SIEM), we provide tailored solutions that strengthen your defenses and improve your overall security posture. We assess your unique risks, consult on the best solutions, and equip you with powerful tools to stay ahead of potential threats.
Take control of your cybersecurity.
Schedule a Consultation
