
Advanced Cybersecurity Solutions: What You Need to Know
Nov 27, 2024
In 2020, a single phishing email led to one of health care’s most significant data breaches. Universal Health Services, one of the largest health care providers in the U.S., experienced a devastating ransomware attack that disrupted operations across hundreds of facilities.
This incident compromised millions of patient records, forced the organization to revert to manual processes, and severely impacted patient care. The financial toll was overwhelming, with estimated losses exceeding $67 million.
This incident highlights a stark reality — cyber threats aren’t just inconvenient—they can halt operations, endanger lives, and destroy public trust
As cyberattacks grow more sophisticated and relentless, relying on a single layer of security is no longer enough. Today’s organizations need a proactive, multi-layered approach to protect everything from system access to cloud data.
In this blog, we will explore the impact of rising cyber threats, the dire consequences of cybersecurity breaches, and advanced cybersecurity solutions every organization needs.
The Impact of Rising Cyber Threats
Today’s businesses operate in an environment of constant digital threats, impacting organizations of all sizes and sectors. As cybercriminals adopt increasingly sophisticated tactics, businesses are at greater risk of attacks that can disrupt operations, steal data, and harm reputations. The global average cost of a data breach in 2024 reached $4.88 million, a 10% increase over the past year.
Ransomware has become one of the most prevalent and costly threats. It was the motivation behind over 72% of cybersecurity attacks in 2023. Alarmingly, 83% of organizations affected by ransomware opted to pay the ransom, with over half of these businesses spending more than $100,000. Beyond financial strain, ransomware attacks have significant operational consequences; 52% of affected organizations reported substantial impacts on their business systems and operations.
These attacks involve long-term infiltration into an organization’s network, allowing hackers to gather sensitive data and monitor activities undetected for extended periods. Without robust defenses, businesses risk financial and operational instability, data loss, and reputational damage.
Consequences of Cybersecurity Breaches for Businesses
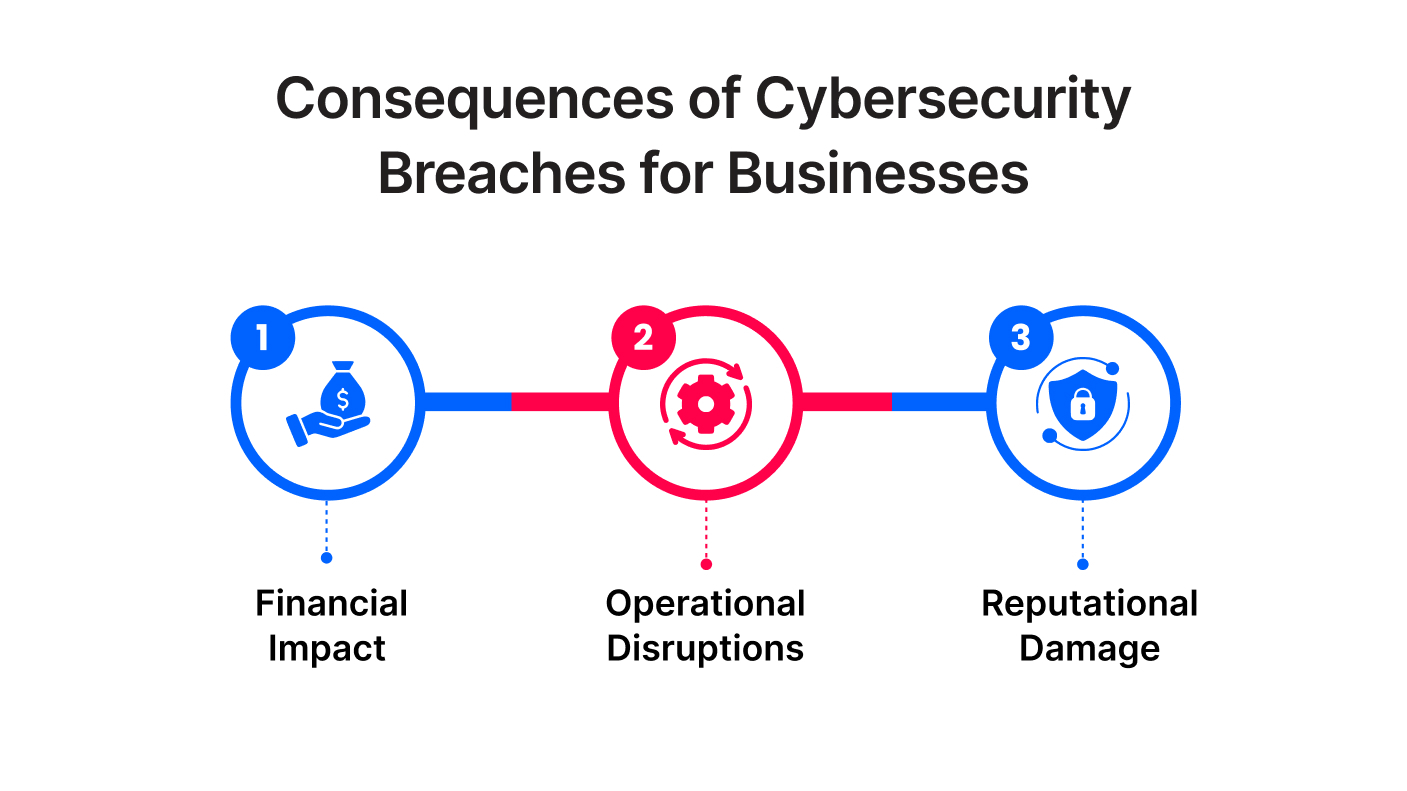
A cybersecurity breach can have severe financial, operational, and reputational consequences, creating ripple effects that impact all areas of a business:
Financial Impact
The economic burden of a data breach goes beyond lost revenue. Costs can include emergency response measures, system restoration, legal fees, public relations consultation, and regulatory fines. In 2024, the average cost per breached record in the United States was $189 for records containing employees' personally identifiable information (PII), making it the highest-cost type of breached data record. For comparison, the cost for records containing customers' PII was $181. Moreover, organizations hit by ransomware attacks sometimes pay large sums to unlock their encrypted data.
Note: STACK Cybersecurity advises against paying ransoms. You cannot trust criminals to keep their word. Paying a ransom doesn’t guarantee you will get your data back. Conversely, it nearly guarantees the cybercriminal will revisit your network in short order.
Apart from paying a hefty ransom, businesses also face downtime. For many companies, downtime translates to lost revenue and productivity, further compounding the financial losses. Lastly, breaches that compromise sensitive data often trigger regulatory scrutiny and fines. For instance, data privacy laws such as GDPR and HIPAA can levy hefty fines.
Operational Disruptions
Cyber incidents often lead to system shutdowns, disrupted workflows, and reduced employee productivity as teams shift focus to damage control. That’s not all; a compromised organization often inadvertently exposes suppliers, partners, and clients to risks. These ripple effects highlight the importance of securing direct systems and interconnected business relationships.
Reputational Damage
Breaches that compromise customer data, such as credit card details or personal information, can quickly erode customer confidence. A survey found that 85% of consumers would likely stop doing business with a company that had experienced a data breach affecting financial information.
Moreover, news of a breach can lead to negative media coverage, impacting brand reputation and long-term revenue losses. Customers expect companies to protect their data, which can lead to irreversible damage to the brand’s image.
Businesses are turning to advanced cybersecurity solutions to address these significant risks to safeguard assets, customer data, and operational continuity. These solutions provide proactive threat detection and enable real-time monitoring to minimize response times and mitigate damage. They also enhance resilience, ensuring business continuity by safeguarding critical systems, protecting data, and preserving trust, even amidst cyberattacks.
Advanced Cybersecurity Solutions
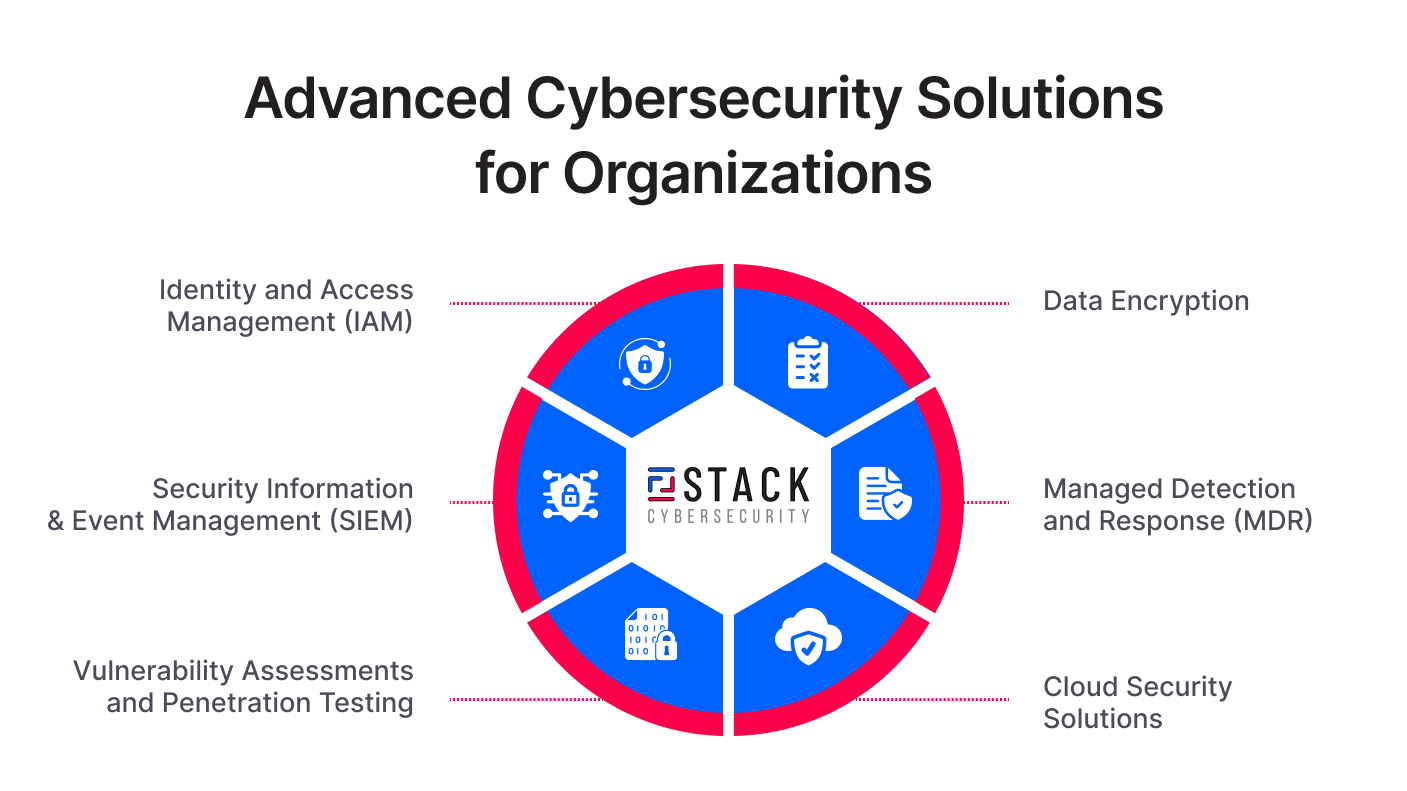
Advanced solutions provide a comprehensive approach, covering everything from identity management to cloud security. Here’s a closer look at a few advanced cybersecurity solutions:
Identity and Access Management (IAM)
Managing access to sensitive information is essential for organizations with multiple users, devices, and systems. Identity and Access Management (IAM) solutions control who can access resources based on roles, departments, and trust levels. IAM tools enforce Multi-Factor Authentication (MFA), implement Single Sign-On (SSO) for streamlined access, and apply the principle of least privilege to limit access to only what each role requires.
Moreover, advanced IAM solutions provide insights into user behavior, flagging unusual activity that might indicate compromised credentials. By securing identities, organizations reduce the risk of insider threats and limit the potential damage of unauthorized access.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) tools are invaluable for centralized oversight across an organization’s security environment. SIEM solutions gather data from multiple sources across the network—such as firewalls, endpoint protection, and servers—to create a comprehensive picture of activity. By correlating events and identifying anomalies, SIEM solutions detect threats in real-time, enabling rapid response before an attack escalates.
Vulnerability Assessments and Penetration Testing
Vulnerability assessments help organizations identify weaknesses across their infrastructure. These assessments analyze applications, networks, and systems for potential security gaps that could be exploited. Your organization can seek help from companies such as STACK Cyber, which conducts penetration testing, where ethical hackers simulate attacks to uncover vulnerabilities before real attackers do.
Conducting regular assessments enables organizations to proactively address risks, patch outdated software, and prioritize remediation efforts. This approach supports a strong security posture and aligns with industry regulations.
Data Encryption
Data encryption is a vital security measure for organizations managing sensitive data—such as financial records, health care information, or proprietary research. Encryption ensures data is protected in transit (e.g., email, file transfer) and at rest (e.g., databases, storage devices), converting it into an unreadable format that can only be decrypted with a unique key. Data encryption is often required for organizations operating in regulated sectors to meet compliance standards like SOC 2 Type 2, NIST 800-171, and CMMC
Managed eXtended Detection and Response (MXDR)
Managed Extended Detection and Response (MXDR) is a comprehensive cybersecurity service that protects your organization from evolving threats. It combines advanced technology with expert human oversight to deliver continuous monitoring, swift detection, and rapid response.
When a threat is detected, MXDR goes beyond simple alerting. It uses human intelligence and advanced threat data to investigate, prioritize, and provide actionable insights. This enables your security team to respond quickly and effectively, minimizing the impact of potential breaches.
Additionally, MXDR functions as a fully managed Security Operations Center (SOC), optimizing your security infrastructure, identifying vulnerabilities, and providing detailed reporting and analytics to track and enhance your security performance. This solution offers a cost-effective alternative to building an internal SOC, ensuring robust protection without the added complexity and overhead.
These advanced cybersecurity solutions are essential for organizations that protect assets, maintain operations, and meet regulatory standards. By adopting a comprehensive approach, organizations strengthen their defenses against evolving cyber threats and uphold their reputation as secure, trustworthy entities
How to Build a Resilient Cybersecurity Strategy for Your Organization
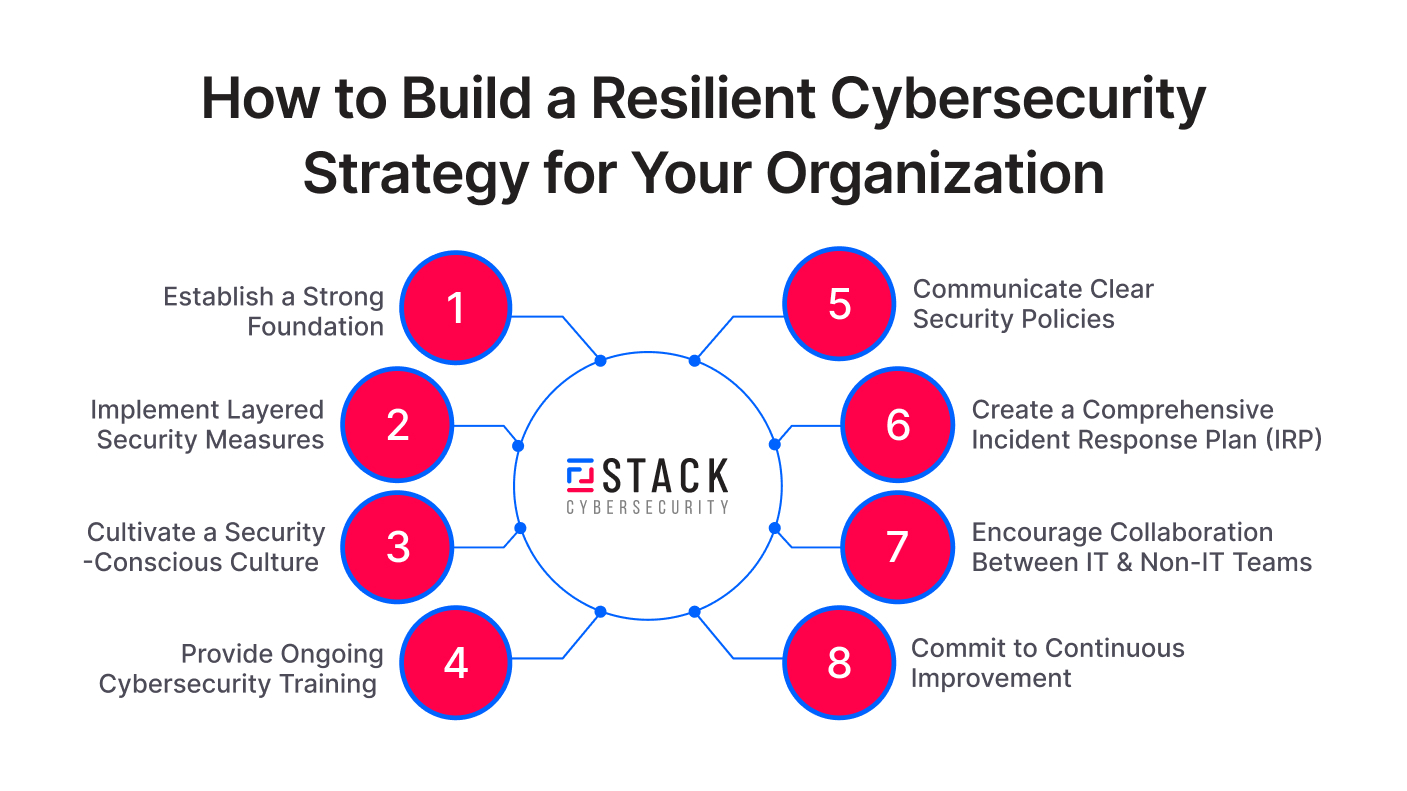
Building a resilient cybersecurity strategy involves more than investing in advanced tools—it requires a holistic approach that combines technology, policies, and people. Here’s a step-by-step guide to developing a strategy that reinforces your organization’s defenses and promotes a security-aware culture.
Establish a Strong Foundation
Your organization can begin by conducting a comprehensive risk assessment to identify vulnerabilities, critical assets, and potential threats specific to your organization. This assessment must include everything from IT infrastructure and cloud assets to employee access points.
Once you have conducted a thorough assessment, your security team can define the organization’s cybersecurity goals, ensuring alignment with compliance requirements, industry standards, and risk tolerance levels.
Implement Layered Security Measures
A resilient cybersecurity strategy uses a multi-layered approach, combining network security, endpoint protection, data encryption, and identity management to create multiple barriers against potential threats. Your organization can consider cybersecurity solutions offered by STACK Cyber, which include a Zero-Trust model, where all users—inside or outside the network—are continuously verified and authenticated before accessing any resource.
Your organization can also benefit from automated monitoring and response solutions that detect anomalies in real time and prevent incidents before they escalate. These solutions and regular vulnerability assessments and updates help keep systems protected even as new threats emerge. Companies like STACK Cyber offer cybersecurity expertise, tools, and solutions to aid your organization in enhancing its security posture.
Cultivate a Security-Conscious Culture
Employees are often the first line of defense against cyber threats, making their awareness and engagement crucial. Your organization must cultivate a security-conscious culture by educating employees on common threats like phishing, social engineering, and unauthorized access. Tools such as phishing simulations, where employees receive fake phishing emails to test their responses, help employees stay alert and recognize real threats.
Additionally, you can conduct regular training sessions to educate your employees on basic, effective cybersecurity practices and emerging threats. These training programs must emphasize the importance of secure password management, recognizing suspicious emails, and safe data-sharing practices.
Communicate Clear Security Policies
Develop clear, organization-wide cybersecurity policies, including acceptable use policies, data handling guidelines, and incident reporting procedures. Your organization must ensure these policies are easily accessible and understood by all employees.
Additionally, organizational policies must encourage open communication, where employees feel comfortable reporting suspected security incidents without fear of repercussions. This proactive approach enables faster responses and demonstrates the organization’s commitment to cybersecurity.
Create a Comprehensive Incident Response Plan (IRP)
A strong incident response plan outlines the steps to take in case of a security breach, minimizing downtime and reducing potential damage. Your organization must define the roles and responsibilities of each team member, ensuring everyone understands their role in a crisis.
Additionally, your organization must run regular drills and tabletop exercises to test the effectiveness of the IRP. This will allow your team to practice their response and identify areas for improvement. Involving employees in these exercises will help them understand the importance of prompt and precise action in protecting organizational assets.
Encourage Collaboration Between IT & Non-IT Teams
Cybersecurity should be a shared responsibility across departments, not solely the responsibility of the IT team. Encourage collaboration between IT and other departments to ensure security policies are practical and aligned with each team’s requirements. Moreover, regular cross-departmental meetings help bridge knowledge gaps, enabling teams to share insights and reinforce a culture of collective responsibility for cybersecurity.
Commit to Continuous Improvement
Cyber threats evolve rapidly, and so should your cybersecurity strategy. Your organization must regularly review and update policies, training content, and technical defenses to stay current with the latest threat intelligence. Cybersecurity is not a one-time effort; resilience depends on your organization’s ability to adapt and improve.
By following the above steps, your organizations can build a resilient cybersecurity strategy that minimizes risk and promotes a proactive, security-aware culture. When every member of the organization understands their role in cybersecurity, the organization becomes significantly more assertive and better prepared to face emerging cyber threats.
Secure Your Business with STACK Cybersecurity

As cyber threats grow more complex, STACK Cybersecurity stands as your dedicated partner for navigating these digital challenges. With 20+ years of expertise in cybersecurity, we address today’s most pressing cybersecurity needs, helping businesses like yours protect what matters most—your data.
Our services go beyond IT support; we bring a powerful stack of industry-leading tools and expertise. From Managed eXtended Detection and Response (MXDR) to Security Information and Event Management (SIEM), we provide tailored solutions that strengthen your defenses and improve your overall security posture. We assess your unique risks, consult on the best solutions, and equip you with powerful tools to stay ahead of potential threats.
Learn More
- SIEM Crucial to Reduce Breach Costs
- How to Maximize SIEM Post-Breach
- How Criminals Attack & SIEM Defends
- 2025 Global Digital Trust Insights
Take the next step in securing your organization: Schedule a Consultation
