Nov. 10 CMMC Deadline Approaches
Sept. 11, 2025

Non-Compliance = Exclusion from the World's Largest Procurement Ecosystem
The Department of Defense is about to enforce one of the most consequential cybersecurity mandates in its history. Starting Nov. 10, 2025, all new contracts will require compliance with the Cybersecurity Maturity Model Certification, or CMMC.
For defense suppliers, this marks the end of the voluntary era. The stakes are enormous, not just for national security but for the billions of dollars flowing through the defense industrial base.
In fiscal year 2024, the Department of Defense received $814.4 billion in appropriations, accounting for 93 percent of the defense spending cap set by Congress. That figure rose in 2025 to $852.2 billion, including emergency-designated funding.
Over the past decade, defense spending has climbed steadily, from $778 billion in 2020 to over $916 billion in 2023. The department now consumes more than 12 percent of the entire federal budget, making it one of the largest single entities in the U.S. government.
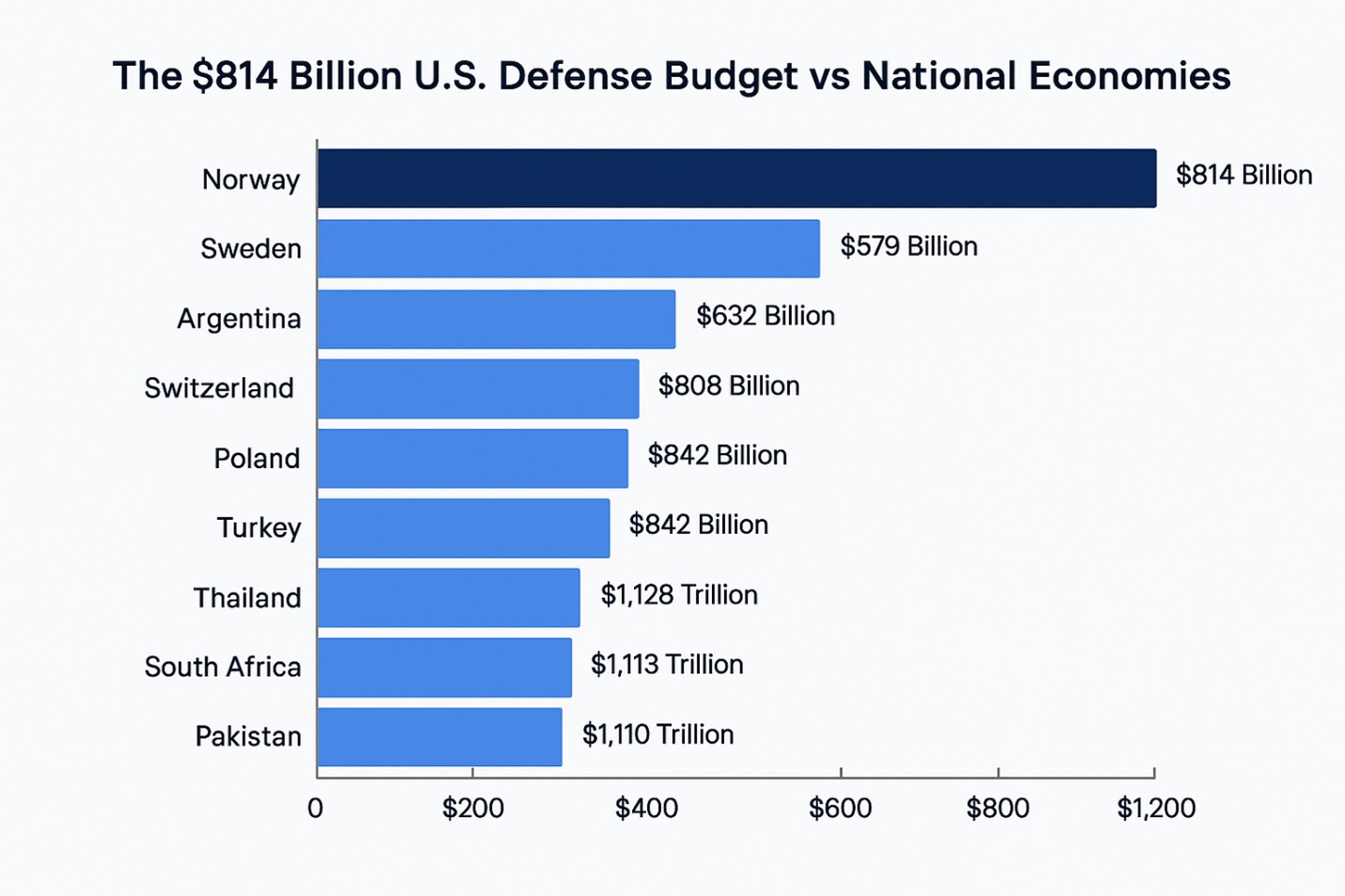
If the Pentagon were a country, it would rank among the top 20 economies in the world.
To put the budget in perspective, see the infographic designed using gross domestic product (GDP) figures based on 2023 estimates from reliable global economic data sources such as the World Bank and International Monetary Fund (IMF). The defense budget figure of $814 billion matches the fiscal year 2024 appropriations for the U.S. Department of Defense.
Supply Chain Security Remains Weak
Despite this scale, cybersecurity across the defense supply chain remains alarmingly weak. Many contractors still lack basic protections like multi-factor authentication (MFA). Others have never conducted a formal cybersecurity risk assessment (CSRA).
Even the Department of Defense itself has struggled with internal security. A 2023 audit revealed thousands of unresolved cyber incidents and inconsistent reporting practices. The Government Accountability Office (GAO) found the department often failed to notify affected individuals and lacked complete data on breaches.
The final CMMC rule, published earlier this year, introduces a tiered certification model based on the sensitivity of data handled. Contractors working with Controlled Unclassified Information (CUI) must undergo expensive and timely third-party audits.
Those handling high-value assets will face direct audits from the Department of Defense. The rule will be phased in over three years, but the November 10 deadline is the first hard stop. Contracts issued after that date will include CMMC language, and suppliers who are not certified will be excluded from consideration.
This is not a theoretical risk.
Defense contracts are the lifeblood of thousands of companies, from aerospace giants to small machine shops. In 2024 alone, the department obligated $290 billion through contracts and financial assistance awards. That money is now tied to cybersecurity readiness.
Suppliers who fail to meet the new standards could lose access to federal funding, jeopardizing their business and the broader supply chain.
Implementation Requires Time, Money, Expertise
The urgency is compounded by geopolitical threats. Nation-state actors have repeatedly targeted defense contractors, exploiting weak links to gain access to sensitive data. The SolarWinds breach exposed vulnerabilities across multiple federal agencies. The CMMC framework is designed to close those gaps, but implementation requires time, money and expertise.
For many suppliers, the path to compliance will be steep.
Costs range from tens of thousands to millions of dollars, depending on the size and complexity of the company. Documentation, infrastructure upgrades, employee training, and continuous monitoring are all part of the equation.
Yet the alternative is worse: exclusion from the largest procurement ecosystem in the world.
Time to Flip Cybersecurity Script
The financial case for cybersecurity has never been stronger. According to STACK Cybersecurity’s internal analysis, companies with mature security programs experience 50% fewer successful breaches than industry peers. For every dollar spent on cybersecurity awareness training, businesses save an average of $4.80 in prevented incidents.
From Cost Center to Profit Protector: How Cybersecurity Saves Your Bottom Line
The average ransomware payment is $1.54 million, while prevention costs a fraction of that amount. Proactive security measures reduce incident response time by 59%, minimizing damage when breaches do occur.
“Cybersecurity isn't just about protection,” said Rich Miller, founder and CEO of STACK Cybersecurity. “It's about prevention, efficiency and long-term savings. Every dollar spent on proactive defense helps our clients avoid costly downtime, regulatory fines and reputational damage.”
One of those clients is Taylor Turning, a precision manufacturer that recently achieved CMMC Level 1 certification with STACK’s help.
“From day one, they made us feel incredibly safe and supported,” said Austin Ritz, compliance manager at Taylor Turning. “They are not just a service provider but a partner who truly cares about our success.”
Taylor Turning’s journey is now featured in a case study on STACK’s website. Their story illustrates how small manufacturers can meet federal standards without sacrificing operational efficiency.
Check out our Taylor Turning Case Study
The Department of Defense has made its position clear. Cybersecurity is no longer a checkbox. It is a contract requirement. And come November 10, the clock runs out.
Where to Report Cybersecurity Breaches
Defense suppliers facing cybersecurity incidents such as a breach, ransomware attack, or data leak have several secure and recognized channels to report the issue. These resources support both anonymous and attributed reporting.
DoD Cyber Crime Center (DC3) via DIBNet Portal
- Purpose: For contractors handling Controlled Unclassified Information (CUI) or COvered Defense Information (CDI)
- How to Report: dibnet.dod.mil
Cybersecurity and Infrastructure Security Agency (CISA)
- Purpose: Report cyber incidents, phishing, malware, and vulnerabilities
- How to Report: cisa.gov
FBI Internet Crime Complaint Center (IC3)
- Purpose: Report cybercrime, fraud, and ransomware
- How to Report: ic3.gov
State and Local Fusion Centers
- Purpose: Regional hubs for threat intelligence and incident coordination
- How to Report: dhs.gov
