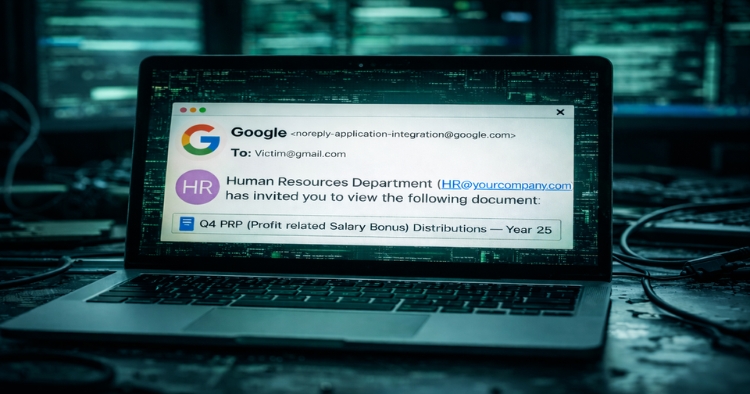
A recent phishing campaign shows that email authentication alone is no guarantee of safety. Threat actors abused Google Cloud Application Integration to send nearly 9,400 phishing messages from a legitimate Google address, fooling traditional filters and putting credentials at risk. Check Point’s analysis found no infrastructure breach at Google. Instead, attackers misused a trusted automation feature to deliver malicious messages at scale.
What Happened
Attackers used noreply-application-integration@google.com, a genuine Google address used by Google Cloud Application Integration, to dispatch phishing messages. Because the messages originated from Google infrastructure, they passed SPF, DKIM, and DMARC checks and retained a clean domain reputation.
Check Point tracked roughly 9,400 of these emails over a two-week period. The messages mimicked routine Google notifications about voicemails and shared documents, using Google’s exact formatting and language that employees see every day. Google confirmed to reporters that the activity stemmed from abuse of its Application Integration service, not from a compromise of Google’s infrastructure.
How The Attack Worked
Links in the phishing emails initially pointed to legitimate Google properties such as storage.cloud.google.com. These destinations reinforced the appearance of authenticity and helped the emails pass automated defenses. After initial clicks, victims were redirected through other Google-controlled domains before landing on a counterfeit Microsoft login page.
Some variants included a fake CAPTCHA. That step increased perceived legitimacy and prevented automated scanners from following the full redirect chain. The campaign aimed to harvest Microsoft credentials rather than deliver malware. Once credentials were entered, attackers could use them to access mailboxes and related systems.
Why Standard Email Filtering Failed
Traditional email defenses place strong weight on sender authentication and domain reputation. Because these messages came from a real Google address and used Google’s infrastructure, they passed standard checks and were far more likely to reach inboxes. The campaign highlights a shift in attacker tactics: instead of spoofing or impersonating domains, threat actors now abuse trusted cloud automation features.
Organizations that rely solely on authentication and reputation are at risk. Modern defenses should include behavioral analysis, full content inspection, and evaluation of link and redirect behavior to detect credential harvesting flows even when a message appears to be from a trusted sender.
Why Manufacturers Were Targeted
Manufacturing relies on email for purchasing, vendor coordination, and payment approvals. Reporting from Check Point indicates that manufacturing accounted for about 20 percent of the targeted organizations. Attackers understand that operational urgency in manufacturing workflows can reduce suspicion, especially when messages appear to come from well-known cloud providers.
A single compromised email account in manufacturing can expose vendor payment schedules, supply chain contacts, engineering specifications, and customer pricing. For organizations with SIEM platforms and EDR, unusual login patterns and anomalous data access are the usual indicators that follow credential compromise.
From Credential Theft To Business Email Compromise
Credential theft is often only the first phase. With mailbox access, attackers can search email histories for invoice templates, payment patterns, and trusted relationships, then craft convincing payment redirection requests using real conversation threads. They can reset passwords on connected systems and move laterally across corporate assets.
Modern business email compromise typically follows this pattern: attacks originate from legitimate accounts issuing plausible requests based on authentic business context. Proper email security controls, user behavior monitoring, and rapid incident response are essential to detect and contain compromised accounts before significant financial or operational damage occurs.
Effective Countermeasures
Defenses must extend well beyond sender verification.
Recommended controls include:
- Trace links through their entire redirect chain, not just the initial URL. Block access to credential-harvesting pages regardless of the originating host.
- Apply behavior-based filtering and content inspection consistently, even for messages from verified providers. Trust may inform processing priority, but it should not remove security checks.
- Flag unexpected authentication prompts that are inconsistent with the service context, for example, Google-originated messages that ask for Microsoft credentials.
- Enforce phishing-resistant multi-factor authentication, such as passkeys or hardware security keys, to reduce the value of harvested credentials.
- Combine advanced email filtering with continuous EDR monitoring and 24/7 SIEM correlation to detect suspicious logins, lateral movement, and data access quickly.
Conclusion
This campaign demonstrates that message authenticity no longer ensures safety. Legitimate emails from trusted cloud services can be weaponized to harvest credentials and enable business email compromise. Organizations should assume that trusted infrastructure can be misused and deploy layered defenses that include behavioral analysis, complete redirect inspection, continuous endpoint monitoring, and expedited incident response.