
Growing Danger of Business Email Compromise
Nov 14, 2024
Business Email Compromise (BEC) attacks are meticulously planned to target specific industries, professions, and individuals, maximizing the chances of cybercriminals accessing sensitive information and money.
BEC attacks continue to pose a significant challenge as cybercriminals constantly refine their techniques and tactics to bypass organizational defenses. Barracuda's latest "Top Email Threats and Trends" report unveils some interesting cyber factoids, including the following:
- Scamming and phishing comprise 86% of social engineering attacks.
- Conversation hacking has increased by 70% since 2022.
- About 1 in 20 mailboxes were targeted with QR code attacks in the last quarter of 2023.
- Gmail is the most abused webmail service.
- Bit.ly is used in nearly 40% of social engineering attacks that use a shortened web address.
- Twitter/X was used in the most attacks in 2020.
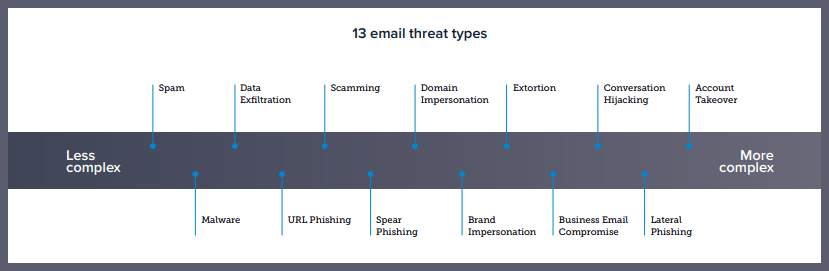
Barracuda identified 13 types of email threats organizations face today. These threats range from high-volume attacks like spam and malware to more targeted threats that utilize social engineering, such as business email compromise and impersonations. The report delves into five of these threat types that Barracuda researchers have been closely monitoring, providing insights and examples of new tactics attackers use to deceive victims and evade detection.
Phased Approach
Unauthorized Access: The initial phase involves gaining access through methods such as phishing, malicious applications, imposter domains, or purchasing credentials from Cybercrime-as-a-Service (CaaS) syndicates. Once access is obtained, cybercriminals enter a period of monitoring.
Monitoring and Fraud: During the monitoring phase, cybercriminals gather crucial information by reading emails, observing trusted networks, and noting financial transactions. Matt Lundy of Microsoft Threat Intelligence explains, “Once a cybercriminal gains access to a target’s inbox, they gain insight into all correspondence, understanding who you communicate with regularly and your communication style.”
Armed with this knowledge, cybercriminals proceed to the fraud stage. They use the gathered information to craft credible stories, enabling them to deceive targets and gain access to funds or sensitive data.
Many global organizations, including Microsoft, have observed a rise in the sophistication and tactics of threat actors specializing in BEC.
Safeguarding Your Organization
With the growing frequency and complexity of BEC attacks, it is crucial for organizations to implement a multi-layered cybersecurity approach. Consider these strategies:
- Employee Education: Regular training can help employees identify and respond to phishing attempts. Awareness is the first defense against BEC.
- Email Verification: Implementing protocols like DMARC, DKIM, and SPF can help confirm the legitimacy of incoming emails and reduce spoofing risks.
- Advanced Threat Protection: Using advanced threat protection solutions can detect and block harmful emails before they reach the inbox.
- Incident Response Plan: A strong incident response plan ensures your organization can quickly and effectively handle a BEC incident, minimizing potential damage.
Watch Our BEC Webinar for More Insights
To explore the topic of BEC further and learn how to protect your organization, we invite you to watch our recent webinar hosted by STACK Cybersecurity in collaboration with Todyl, our Security Information and Event Management (SIEM) vendor.